SOC (Security Operations Center) is essentially going to be necessary for any company in today’s world. Whether that’s just the only employee regularly running through a checklist that reviews the antivirus, backing up data, and making sure nothing is broken, or whether that’s a dedicated team of professionals who spend all day reviewing a company’s security posture, it’s a necessity. The internet is constantly vulnerable to attack and if a company is not ready for an attack, it will eventually come and it could very well be a game changing event.
So what does a SOC do? Well, it’s a Center for all things related to the security of a company (gasp in shock). If a company is considering a SOC for the first time, they have to define what the SOC will do and attempt to get everyone on board with that program. Ideally, a SOC is going to monitor threats, manage information that relates to the security of the company, defend against attacks, attempt to find vulnerabilities before malicious “others” find them, and then regularly review those steps to see how successful they are.
Companies are no longer measuring their cybersecurity setup on a “are we secure or not” basis, but more on a continuum scale of “how mature is our cybersecurity?”. Thus, we see a lot of training and professionals in this field talking about the maturity of a company’s cybersecurity program. Once a SOC is established, they then have to decide how to implement the basic steps of cybersecurity: identify, protect, detect, respond, and recover.
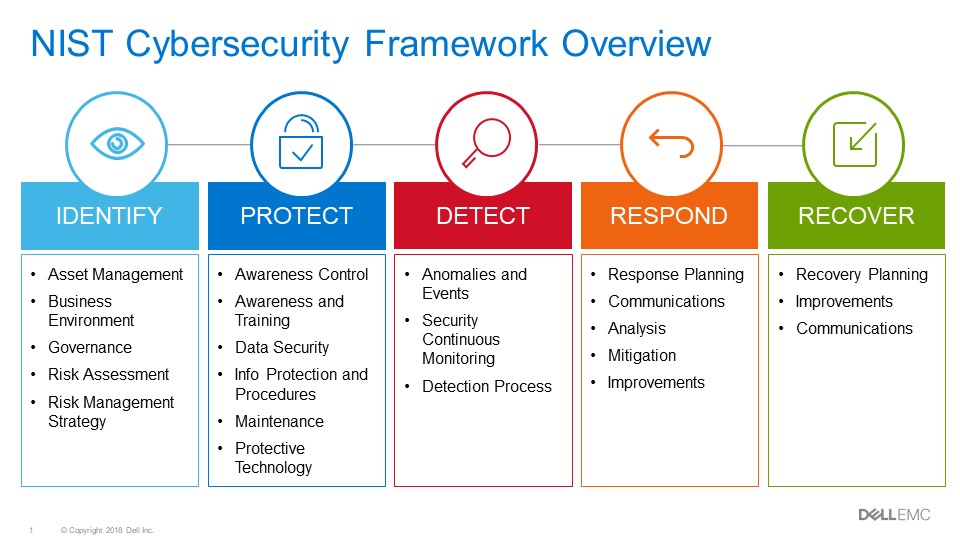
Each of these steps requires a review of companies processes and assets and an evaluation of what needs done. Each company’s processes and steps are different as each company has to decide how inconvenienced they will be for the sake of their level of security. Security has an adverse effect on convenience. So business processes must be a part of the consideration of what a SOC team delivers (especially if you want buy in from those who would support it).
The company’s resources also determine what a SOC does and doesn’t do. If there is not much in funding for a SOC, then it has to keep things simple using free or inexpensive tools and limiting the scope of responsibilities for those running the SOC. It may not be feasible to have someone watching all the various networks, analyzing every point of entry’s risk assessment, and attempting to respond to every malicious email or security question.
Ultimately a SOC is just a place for a company to centralize their security operations (no need to gasp again). Dictated by multiple factors, this will look differently across the board. But it is something every company should be thinking about.

Leave a comment